The UMBC Cyber Defense Lab presents
Hardware Security Kernel for Managing Memory and Instruction Execution
Patrick Jungwirth, PhD
Computational and Information Sciences Directorate
Army Research Lab, Aberdeen Proving Ground, USA
12–1 pm Friday, 28 February 2020, ITE 227, UMBC
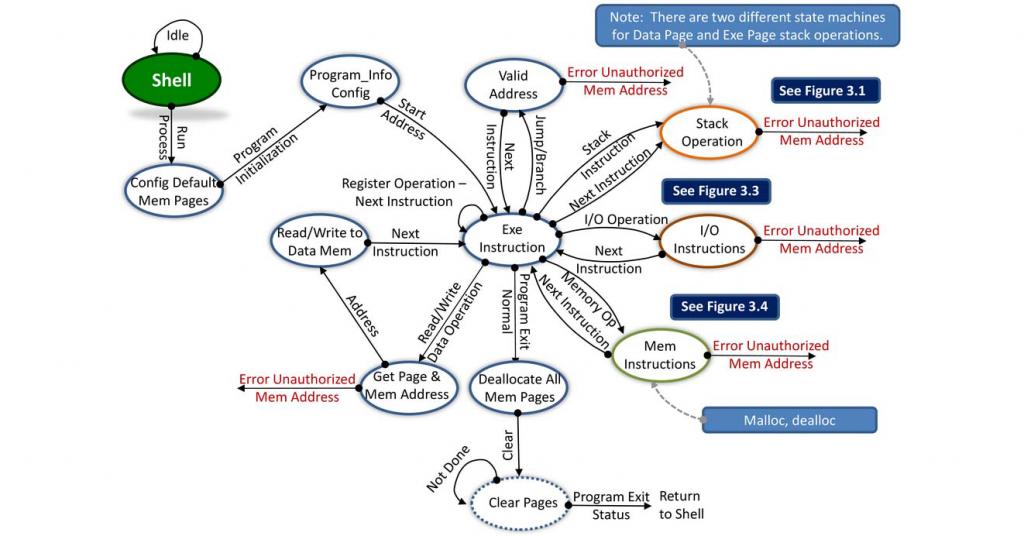
The cybersecurity world faces multiple attack vectors from hardware-level exploits, including cache bank malicious operations, rowhammer, Spectre, Meltdown, and Foreshadow attacks, and software-based attacks including buffer-overflows, et al. Hardware-level exploits bypass protections provided by software-based separation kernels. Current microprocessor execution pipelines are not designed to understand security: they treat malicious instructions, software bugs, and harmless code the same. This presentation explores adding a hardware-level security monitor below the execution pipeline [1,2,3].
[1] P. Jungwirth, et al.: “Hardware security kernel for cyber-defense,” Proc. SPIE 11013, Disruptive Technologies in Information Sciences II, 110130J, Baltimore 10 May 2019); https://doi.org/10.1117/12.2513224
[2] P. Jungwirth, and J. Ross: “Security Tag Fields and Control Flow Management,” IEEE SouthEastCon 2019, Huntsville, AL, April 2019.
[3] P. Jungwirth and D. Hahs: “Transfer Entropy Quantifies Information Leakage,” IEEE SouthEastCon 2019, Huntsville, AL, April 2019.
About the Speaker. Dr. Jungwirth is a computer architecture researcher at the Army Research Lab. Previously he worked for the Aviation and Missile, RDEC in Huntsville, AL. Currently, he is researching hardware state machines to provide simple operating system support (monitor) and control flow integrity in hardware. Dr. Jungwirth is co-inventor of the OS Friendly Microprocessor Architecture, US Patent 9122610. The OS Friendly Microprocessor Architecture includes hardware security features for an operating system and supports near single-cycle context switches in hardware. Email:
Support for this event was provided in part by the National Science Foundation under SFS grant DGE-1753681.
The UMBC Cyber Defense Lab meets biweekly Fridays. All meetings are open to the public.
Upcoming CDL Meetings:
Mar 13, Hasan Cam, autonomous agents
Mar 27, Dan Yaroslaski, cybercommand
Apr 10, Russ Fink (APL), ransomware
Apr 24, TBA
May 8, Jason Wells, law enforcement
May 22, Spring SFS Meeting at UMBC, 9:30am-2pm, ITE 456